Security assurance starts here.
Accelerate hardware resilience through
proactive vulnerability detection
Cycuity: Your Answer to Advanced
Security Verification
Cycuity redefines security verification for the hardware development lifecycle. Our Radix technology was created with a singular focus on security, and helps you identify and mitigate hardware vulnerabilities that other techniques might miss, including at the microarchitecture, full system-on-chip (SoC) levels, and firmware.
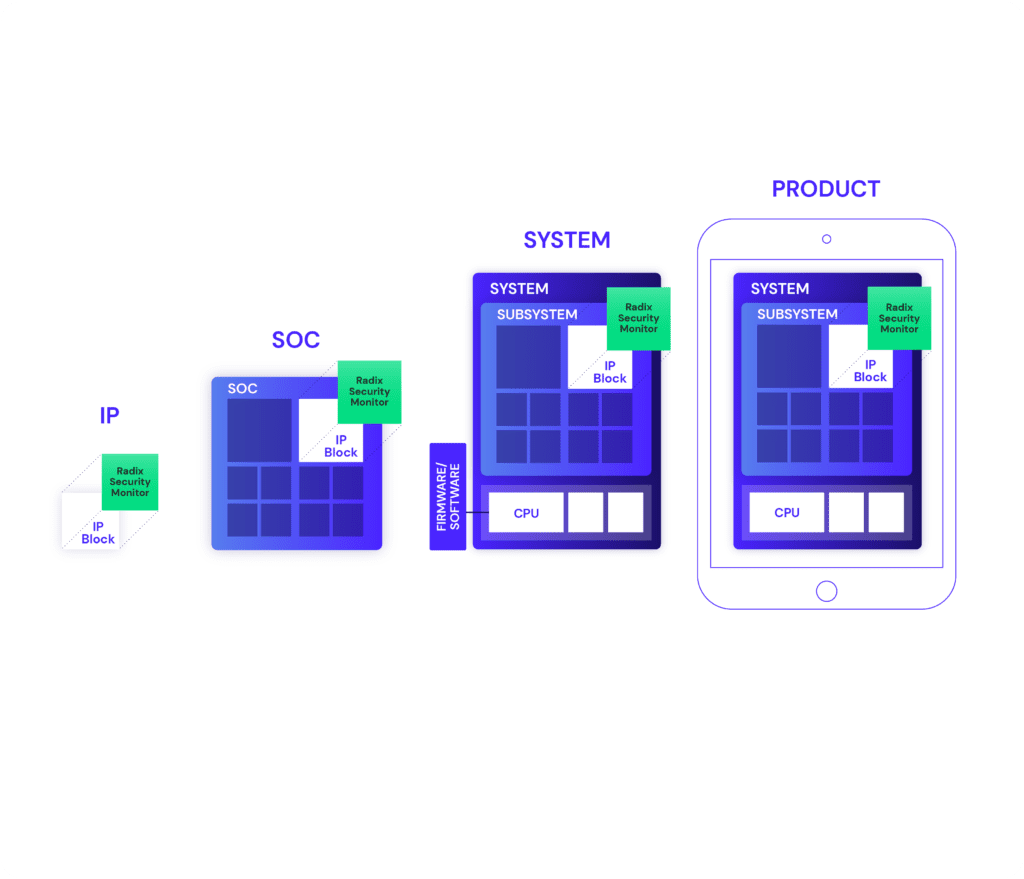
Prevent late-stage and costly security surprises
Hardware security threats are far costlier to remediate than software incidents. Radix accelerates vulnerability detection to ensure hardware security is an integral aspect of chip design and development. Proactively mitigate risk with scalable and systematic security verification — from individual IP blocks to full systems, including software.
Gain unparalleled security insights
With Radix, teams can quickly explore and understand the behavior of security functions and gain insights into unexpected behaviors of secure assets. In addition to in-depth security visualization and analysis capabilities, Radix’s information flow technology tracks and traces locations and flows of your secret assets — ensuring the absence of security vulnerabilities.
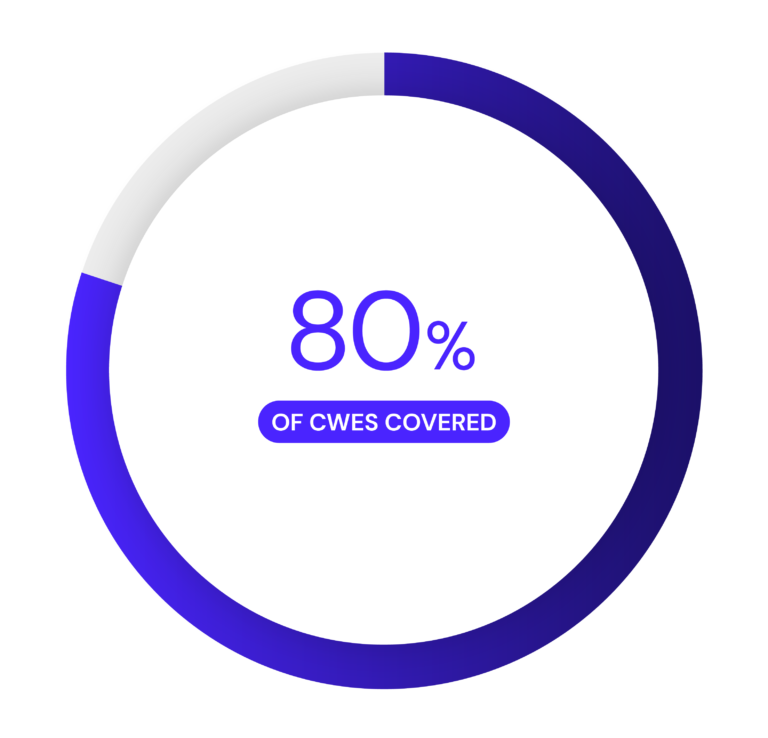
Eliminate hidden and unknown security risks
Protecting your assets against security weaknesses enables confident verification against a greater range of security risks. Radix systematically detects known and evolving security weaknesses—including those documented in best-practice standards like the MITRE-driven Common Weakness Enumeration (CWE)—ensuring they don’t end up in your final design.
A comprehensive approach to security verification.
Radix integrates with and augments your existing verification flows to help you identify and address security risks at every step of the hardware development lifecycle.
Industries We Serve
Hardware Security Maturity
Hardware security is a journey.
You don’t need to transform your entire design and development process on day one to make an immediate impact with Radix.
We’ll partner with you to find quick security insights and start you on your journey to hardware security maturity.
Where are you in the maturity of your hardware security program?

The world’s top companies trust Cycuity for next-level hardware security.
“Cycuity’s Radix series addresses our need for concurrent firmware and hardware validation to ensure we deliver the most secure products to the markets we serve, including aerospace and defense, automotive, and data center.”
Gaurav Singh
CORPORATE VICE PRESIDENT, AMD
Featured Resources
Level up your hardware security today.
Get the confidence of end-to-end hardware security assurance throughout the product lifecycle. Contact us today to see how.